PV falls victim to Google “phishing” scheme
PV one of many organizations effected by attack
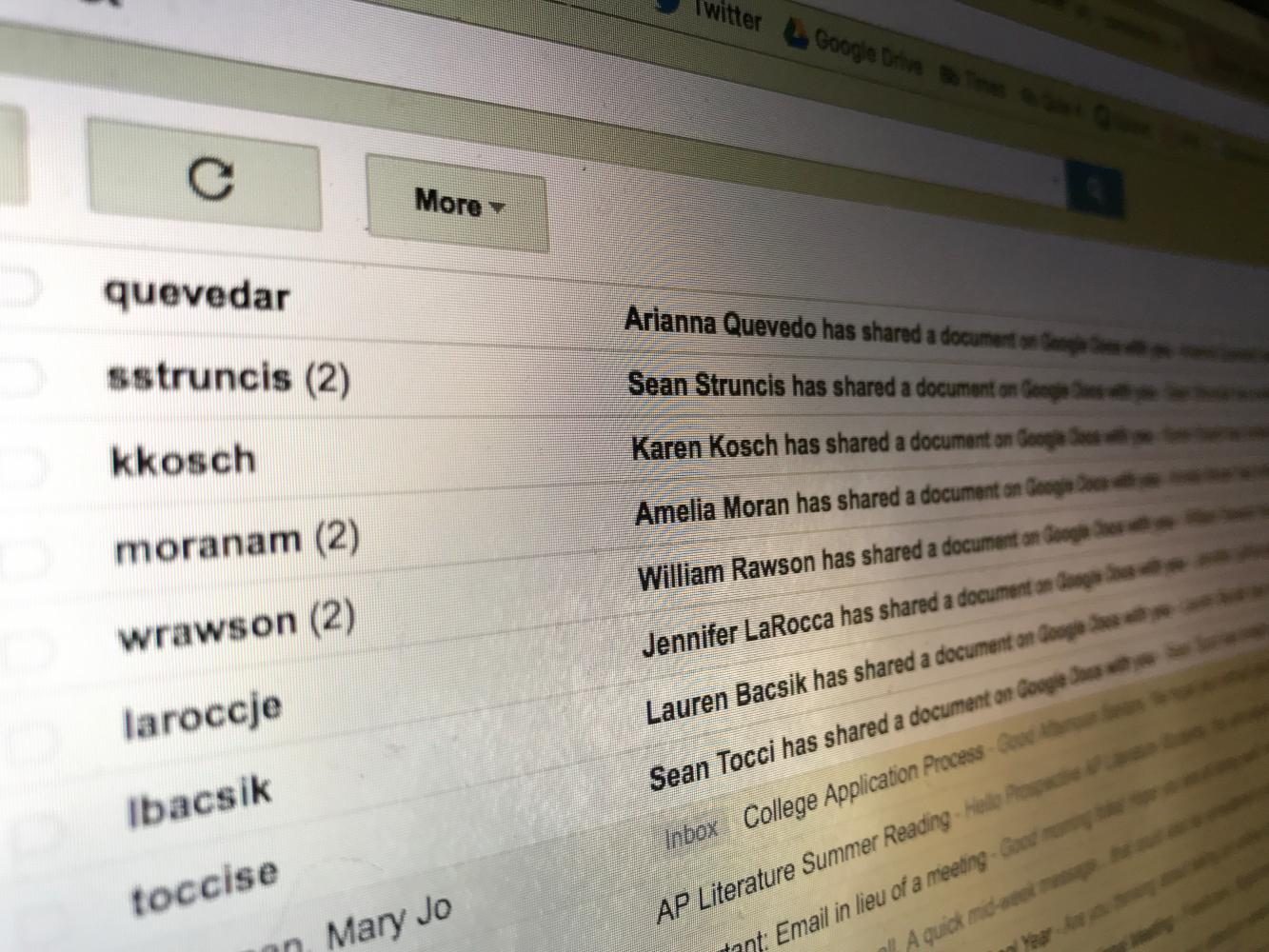
Pascack Valley students and faculty received several fraudulent emails from peers Wednesday that claimed to be sharing Google Docs.
The PVRHS district, alongside much of the nation, was victim to an international email phishing scheme conducted against Google users Wednesday afternoon.
“We were on the phone [with Google] within two minutes, explaining to them what we saw, sending them information, and working with them to solve the problem,” said Mr. Paul Zeller, the Director of Instructional Technology in the PV district.
Phishing schemes usually send an email to users that pretends to come from a legitimate source and redirects users to a page that tries to trick them into entering their usernames and passwords.
However, according to Google Software Engineer and Hillsdale resident Igor Peshansky, this attack was different. The source of the scheme attempted to trick users into giving permission to read, delete, and send emails to a third-party Google app, as well as allowing the app to manage contacts. This attack did not give the extension access to user passwords. While the hacker has not been identified, the email account that developed the third-party app, [email protected], has now been disabled.
“The hacker doesn’t need to know your password,” Peshansky said. “This is the kind of attack that is dangerous because if you don’t know that you gave your permission, they can still access your account.”
According to an email sent out Zeller, the first of these emails was found in the district at 2:32 p.m. Victims of the scheme received an email saying that a person on their contact list had shared a Google Doc with them. Those who clicked on the link to open the document had the extension installed onto their email accounts, which then sent the same email to all of their contacts.
Within 20 minutes of discovering the attack, the Technology Department discovered the extension was approved on several district email accounts and revoked permission for the app to access emails manually.
“Once we figured out what it was doing,” Zeller said, “we stopped it, cleaned it up, explained to Google what we were doing, and then they said they were going to take care of it systematically.”
According to Peshansky, Google took steps to prevent, mitigate, and educate about the attack. They first blocked the addresses sending the false Google Doc emails and sent out statements to news sources as well as tweeting from the Google Docs Twitter account about the scam. Eventually Google blocked the app, revoking its permissions.
While most people at PV did receive an email, according to an email that Zeller sent to the PV community, only 27 people throughout the district actually clicked on the link and had the extension installed onto their computers.
Yesterday morning the Technology Department went through the emails of the people who clicked on the link and did a final manual check in order to ensure the accounts were not still attached to the app.
While some individuals in the district have been affected by phishing schemes in the past, this was the first widespread, systematic phishing scheme that has affected the Pascack Valley District.
PV currently uses the email server “Google App Suites,” a management system for corporations that gives administrators control over permissions and restrictions on the email accounts. Prior to the 2015-2016 school year, the district used Novell Groupwise, now known as Micro Focus GroupWise, which was less susceptible to this type of targeting because it was not a managed environment. According to Zeller, it’s likely that the hacker was targeting managed environments due to their size.
“A person targeting a managed account wants to hit as many people as possible,” Zeller said. “Managed environments will spread quickly because typically there are groups.”
Peshansky said that it is likely that the hacker was mainly targeting large corporations using Google management systems in an attempt to gain access to emails.
While this was a complex scheme, there were signs that the emails were not legitimate.
The emails were sent directly from users’ email addresses, with the pascack.org domain name, rather than the specific “doc.google.com” domain name that is normally used. The emails were addressed to [email protected] and merely BCC’d recipients of the emails. Along with this, if users were to hover over the button that said “Allow,” the link did not lead to Google Docs.
“This is the kind of attack that only be really successful and really widespread once because people will be burned and then they will know,” Peshansky said.
Because Google has not suggested that users should change their passwords as a precaution against this particular phishing scheme, the district is not requiring a password change. However, Zeller recommends that those who clicked the link to open the document do change their passwords.
“My feeling is it can’t hurt to change your password,” Zeller said. “It’s a little inconvenient you have to stop by [the Technology Department], and it’s a little inconvenient for a couple days you have to remember a new password, but how much bigger of a problem is it if someone has access to your account?”